SOC 2 Type 2 Certified
Penny has completed the full SOC 2 Type 2 certification, including an audit performed by qualified evaluators from an independent third-party auditing firm. This certification is crucial as it demonstrates our commitment to maintaining the highest standards of security, availability, and confidentiality for our customers’ data.

World-class security infrastructure
Architecture
Authentication
Scalability
Platform
Architecture
The Penny Enterprise platform is built to the highest security standards. Penny and its data are completely isolated and receive rapidly deployed security updates without customer interaction or service interruption.
Penny Hyperscale cloud – world-class architecture leveraging simultaneously active and redundant systems that allow the overall system to survive outages and remain operational.
Platform Security – holistic security approach is built into Penny operations, encompassing hardware and infrastructure, systems, applications, transmission and storage.
Robust API – highly secure, flexible and robust API enables Penny to connect to any of your existing and future back-office systems.
Security best practices
- Secure and reliable infrastructure. Penny uses Amazon Web Services (AWS) for the hosting and production environments. AWS centers are monitored by 24×7 security, biometric scanning, video surveillance and are fully SOC certified.
- Separation of machines housing critical data from machines running front end applications
- Strict access controls to each data piece defined by both Penny and the client
- An audit system which records each transaction built into the core of the product
- Physical restriction to machines is only allowed by authorized vendor, not even Penny employees can physically access them
Technical Architecture
How does Penny connect and integrate with my environment?
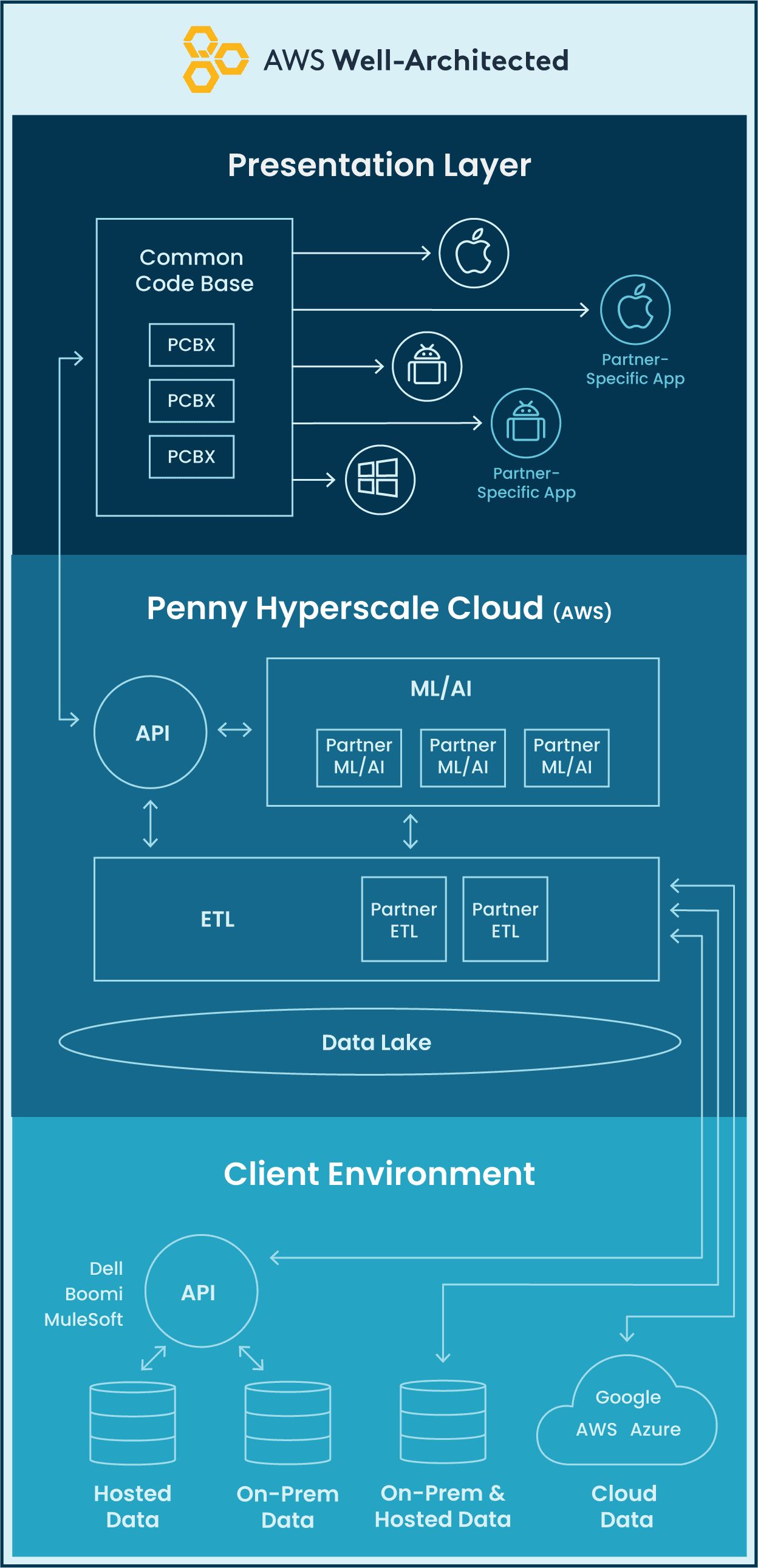
Data Privacy
Data ownership – Your data belongs 100% to you. Access to customer data is limited to authorized employees.
Data usage – We only use customer and consultant data to provide our service.
Data Encryption – Penny encrypts data at rest and data in transit between devices and networks for all of our customers. Data is encrypted at rest using industry standard AES-256 encryption algorithm
Development policy
The Penny development team uses a standardized process to ensure changes are made securely and reliably, with a focus on quality.
- All changes begin with a pull request from a local development branch to a QA environment.
- A code review is done by a senior developer before any changes are merged into a QA environment.
- All changes are tested in QA, and another run of testing in UAT.
- After rigorous UAT testing, code is pushed from UAT to production. All code migrations occur across SSL.
- Code deployment keeps all software up to date with the latest security patches.
Compliance standards
We are taking every step to ensure our people, processes and technology are compliant with any laws, rules, regulations and standards. For any questions about information and data security, please contact privacy@pennyapp.com
GDPR
Penny is committed to helping users understand their rights and obligations under the General Data Protection Regulation (GDPR).
CCPA
We operate in accordance with data protection policies that are based on privacy principles that underlie the California Privacy Act (CCPA).
SOC 2 Type-2 Certified
Penny has completed the full SOC 2 Type 2 certification, including an audit performed by qualified evaluators from an independent third-party auditing firm. This certification is crucial as it demonstrates our commitment to maintaining the highest standards of security, availability, and confidentiality for our customers’ data.
What is a SOC2 report and why is it important?
Service Organization Controls (SOC) is a detailed level of controls-based assurance covering five Trust Services Criteria (security, confidentiality, integrity, availability and privacy). It ensures service providers securely manage the retrieval, storage, processing and transfer of data to protect the interests of both the client’s organization and privacy of their customers.
What Compliance Controls are included in SOC2?
Security
To ensure protection against unauthorized access, internal controls need to mitigate the potential abuse or misuse of the platform, theft or the unauthorized removal of data, and disclosure of personal information.
Confidentiality
To ensure the restriction of confidential data, internal controls need to define security and data protection procedures.
Processing Integrity
To assure the intended purpose of a platform is achieved, internal controls need to monitor data processing and quality assurance procedures. The purpose focuses on processing the right data at the right time.
Availability
To control the access to a platform as per the contract and/or service level agreement with customers (specifically regarding the minimum acceptable level of performance), internal controls need to monitor performance and availability.
Privacy
To control the collection and use of personal information, internal controls need to support the protection of personal information from unauthorized access.
How is Penny AI addressing the Compliance Controls?
Policies procedures and guidelines
We take technical, contractual, administrative, and physical security steps designed to protect Personal Information provided to Penny. We document and reinforce data protection in how we conduct our business.
Operational processes
We continue to review and adapt our internal processes to further mitigate any privacy risk.
Third-party risk management
We continually review vendors and integration partners’ security policies and procedures.
Data retention
We have implemented procedures designed to limit the dissemination of Personal Information to only such designated staff as are reasonably necessary to carry out the stated purposes we have communicated to you.
Data residency
Penny App stores its data on servers in the United States and Ireland. Penny relies heavily on Amazon Web Services (http://aws.amazon.com) for most of our infrastructure. Other companies which utilize this infrastructure include FDA, Netflix, Adobe, Suncorp and Dow Jones.
Terms & Conditions
We review our Terms and Conditions on a regular basis, providing access to the documentation on our website.
Data breach notifications
We have developed and follow Penny AI incident response policies.